What is Spooling in Cyber Security? Best Practices, Risks & Advantages
In the world of cybersecurity, many technical terms get thrown around daily. One such term that is important for cybersecurity professionals and enthusiasts to understand is “Spooling.” But what is Spooling in cyber security?
Spooling is a concept that relates to temporarily storing data or files for processing at a later time. Having a solid grasp of Spooling, including what is data Spooling in cyber security and the Spooling meaning in cyber security, is critical for anyone involved in protecting systems and information.
In this guide, we will provide an in-depth overview explaining Spooling in cybersecurity. We will cover fundamental definitions, examine typical Spooling operations, discuss how Spooling works, and outline why awareness of this mechanism is vital for experts in the infosec domain.
Table of Contents
Explanation of Spooling
-
Definition of Spooling
Spooling is the process of temporarily storing or buffering data in a queue or staging area until resources become available to process it. The acronym Spool originates from Simultaneous Peripheral Operation On-Line. The name “Spooling” harkens back to the literal reels or spools of magnetic tape used for data storage on primitive
computers.
-
History and Evolution of Spooling
In the early days of mainframe computing, peripheral devices like printers and card readers were painfully slow compared to central processing units. This severe mismatch in speed was a thorn in the side for programmers and users alike. Jobs that read punched cards or generated reams of printed output directly were hamstrung, forced to trudge along at the snail’s pace of the mechanical devices.
The first Spooling programs, like IBM’s aptly named “SPOOL System,” provided respite by copying data from punched cards to magnetic tape in the background. This freed up the CPU to work on other tasks instead of idly waiting on the I/O devices. The data was then spooled back to cards and printers from the tapes. Hard disks, with their quicker access times, began replacing magnetic tape for Spooling purposes in the 1960s. By the 1970s, disk Spooling ruled the roost, having largely supplanted the use of tape.
-
Different Types of Spooling
There are a few common Spooling mechanisms:
-
Input Spooling
Input Spooling grabs data from input devices, prepares it for processing, and places it in a job queue. This allows input to be captured at high speeds without bogging down the system or tying up valuable processing resources. Input Spooling can decrease job run times, maximize sequential task execution, and boost throughput from scanners, keyboards, and other input hardware.
-
Output Spooling
Output Spooling routes job results to disk storage instead of directly to printers or diskettes. This allows the jobs generating the output to march on without missing a beat, unencumbered by the speed or availability of physical output gadgets.
Output Spooling also enables efficiently producing results on multiple outputs – say printers and diskettes – from the same job. It works its magic by initially shuttling all printer-bound output to disk storage, breaking the potential logjam imposed by pokey printers.
In addition to these two primary forms, Spooling takes on specialized roles for particular applications:
- In email systems, Spooling seamlessly captures incoming and outgoing messages behind the scenes before routing them to recipients. This prevents bottlenecks that would otherwise clog productivity.
- Network Spooling intelligently queues data when connectivity is disrupted, then transmits the backlogged traffic once the link is restored.
- Virtual Spooling smooths workflows by holding data destined for virtual printers and devices.
So, in essence, Spooling acts like a revolving door, optimizing traffic flow between faster and slower systems. No matter the implementation, the essence of Spooling is optimizing throughput by intelligently staging data for asynchronous processing. This concept remains relevant even as technology has radically evolved.
How Spooling Works?
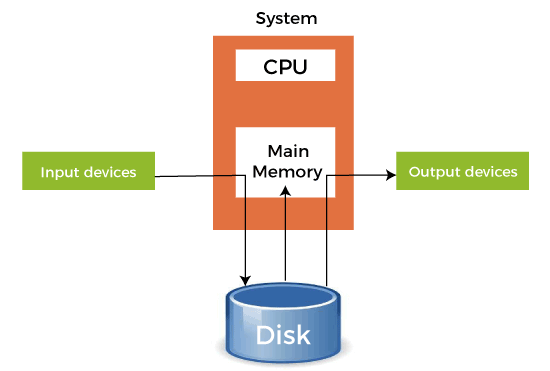
Spooling allows multiple processes to simultaneously write to a single output device by acting as a “traffic cop” to coordinate and schedule the jobs. It uses a queuing algorithm to take in print jobs and hold them in memory buffers or disk storage.
For example, several print jobs can be sent to the Spooling system and held in memory or on disk. The spooler then manages the jobs, sending them to the printer one by one when it is available. This avoids collisions and allows much more efficient utilization of the printer.
Spooling leverages temporary storage areas to stage data as a pit stop, mitigating speed mismatches between data producers and consumers. For example, a speed demon CPU churning out pages at 1000 pages per minute can easily overwhelm a snail-paced printer managing 10 pages per minute. Spooling swoops in to save the day – storing the fast and furious output to disk while methodically throttling the data flow to the plodding printer. This coordination keeps bottlenecks at bay and everything running smoothly.
Spooling also rides to the rescue when Internet connectivity is interrupted by patiently accumulating and queuing up data until transmission can resume. It enables glitch-free audio/video streaming by breaking content into digestible chunks in advance for smooth playback. So, in essence, spooling acts as a shock absorber and pacing mechanism, optimizing divergent speeds across the finish line.
Spooling in the Context of Cyber Security
Spooling plays an integral role in cybersecurity by regulating traffic flows to avoid overloading critical systems. It acts like a safety valve, preventing malicious data floods from wreaking havoc. The queuing and throttling of Spooling provide resilience against denial-of-service attacks and other threats.
Intelligently buffering and pacing data flow allows security systems to operate at peak efficiency. Spooling smooths out surges, facilitating analysis of suspicious traffic without missing a beat. It enables cyber defense tools to stick to the task at hand instead of constantly playing catch-up.
Securely staging data for asynchronous processing also contributes to protecting sensitive information. Encrypted Spooling queues shield data at rest from prying eyes. And pacing data transmission avoids leaks from overfilled communication pipelines.
Understanding Spooling’s role as a controlled data release valve and enabler of efficient threat analysis provides critical insight into system safeguards. Spooling is a key cog in the intricate machinery that keeps pernicious threats at bay in the modern threat landscape.
Real-life Examples of Spooling in Cyber Security
-
Print Nightmare (2021)
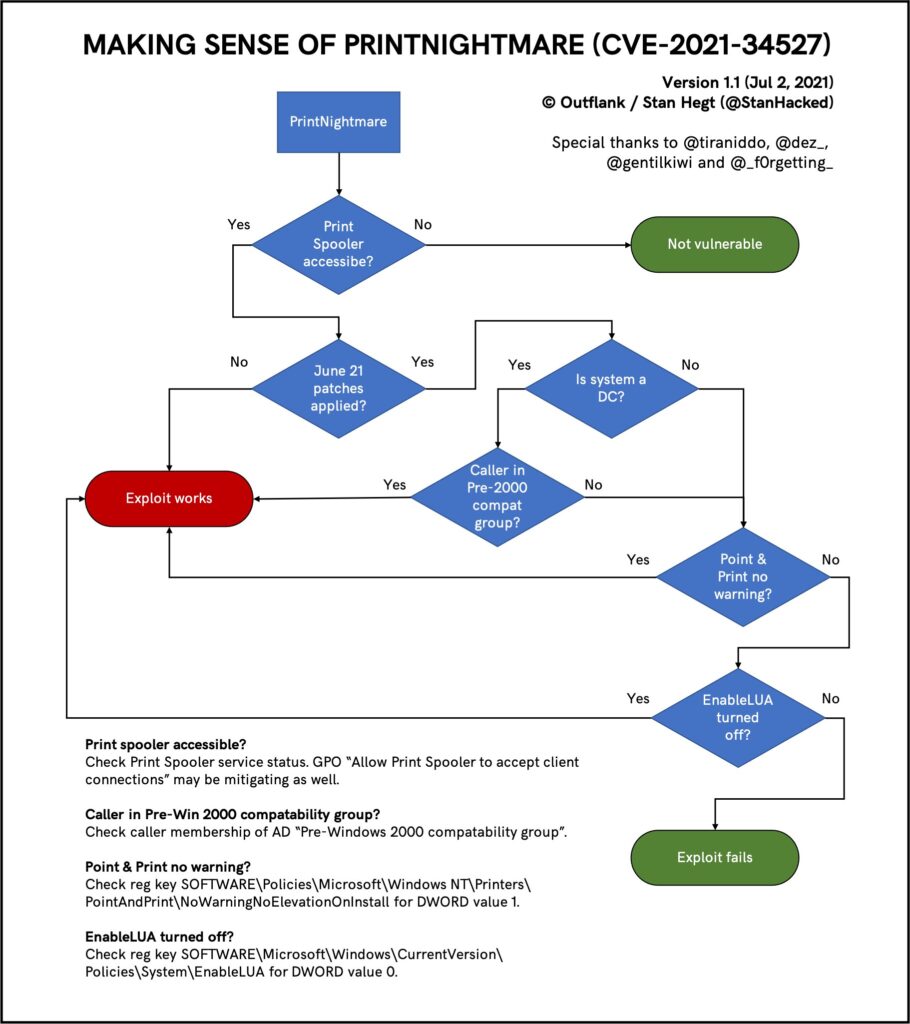
The PrintNightmare vulnerability highlighted the danger of unpatched Spooling services. In June 2021, researcher Zhiniang Peng publicly disclosed a zero-day bug in Windows’ print spooler component.
Alarmingly, Microsoft’s latest security update had failed to patch the print spooler flaw. This oversight allowed attackers to exploit the bug to remotely execute malicious code as the all-powerful SYSTEM user on vulnerable Windows machines. Like moths to a flame, hackers could use PrintNightmare to easily infiltrate networks.
Microsoft eventually rated PrintNightmare as a critical remote code execution risk and scrambled to release fixes. However, flaws in their initial patches meant the cat-and-mouse game continued as new exploits emerged. The PrintNightmare debacle underscored the perils of lagging spooler security upkeep.
-
Operation Aurora (2009)
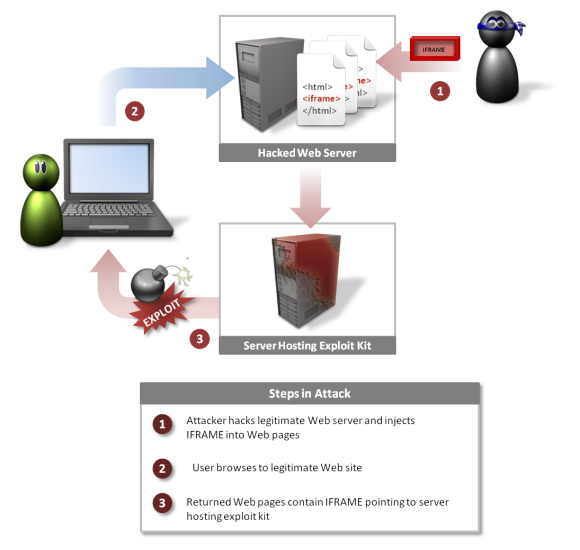
Operation Aurora exemplified the havoc that could be wreaked by weaponizing vulnerabilities in Spooling services. This wave of cyberespionage targeted dozens of major corporations in 2009-2010. The attackers used spear-phishing emails to bait users into clicking malicious links.
These boobytrapped web pages exploited a previously unknown Internet Explorer vulnerability to silently gain a foothold on systems. From there, the hackers could fan out across the network thanks to deep flaws in Adobe’s PDF print spooler service. By tricking users into opening rigged PDF documents, the attackers triggered secret backdoor access to install malware and exfiltrate intellectual property.
Operation Aurora showcased how cyber spies could pull off an Ocean’s Eleven-style heist by chaining together spooler vulnerabilities with social engineering and zero-day browser bugs. The resulting breach devastated Google and many other high-profile companies as the hackers made off with sensitive data.
-
Shamoon (2012)
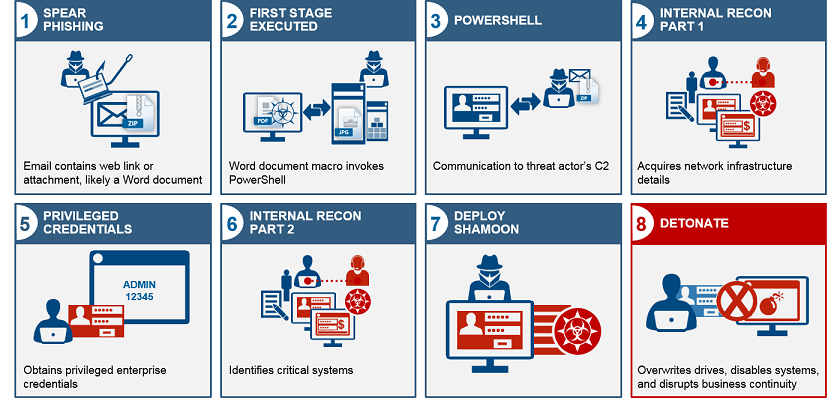
The Shamoon incident in 2012 demonstrated how sabotaging spoolers could cripple operations. This destructive malware infiltrated multiple energy companies in the Middle East by compromising insider credentials.
Once inside the network, Shamoon unleashed its payload by weaponizing the print spooler service. It overwrote critical system files with corrupt data to render infected computers utterly unusable. Shamoon also deleted documents, spreadsheets, emails, and other mission-critical information stored on over 30,000 endpoints across the victim networks.
Adding insult to injury, the malware taunted victims by replacing deleted files with images of burning American flags. It also reported back to the attackers on the tally of annihilated files to boast about the damage inflicted.
By ravaging print spoolers, Shamoon paved a path of disruption through its victims’ systems, causing tremendous financial impact. The extensive data destruction and operational downtime crippled major energy companies for weeks.
This incident spotlighted the havoc that could ensue when attackers turn a basic Spooling service against its owners. It drove home the need for air-tight spooler security to prevent insider threats from unleashing a world of hurt.
These examples showcase the perils of Spooling vulnerabilities and the critical need for air-tight security.
Understanding What Are Spooling Attacks?
-
How Spooling Can Be Used Maliciously
Spooling’s ability to temporarily store and queue data for asynchronous processing can be abused by attackers to compromise security in sneaky ways. For instance, a crafty hacker could exploit Spooling to intercept sensitive documents or quietly distribute malware across a network.
Let’s imagine a scenario where a company uses print Spooling on its corporate servers. An attacker manages to compromise the print server and lie in wait, masquerading as the authorized print spooler service.
Employees send confidential financial reports to the office printer as usual. But these print jobs are detoured through the counterfeit spooler controlled by the attacker. Patiently biding time in the queue, the hacker can then inspect the spool files, stealing financial data or customer records straight from the print jobs.
From the outside, everything appears normal. But behind the scenes, the spoofed spooler is the perfect trap to covertly siphon sensitive documents. The attacker takes advantage of legitimate Spooling functions for illegitimate purposes.
This illustrates how on-the-sly threat actors can potentially leverage intermediate Spooling storage and processing to carry out devious operations like data exfiltration, malware distribution, or system sabotage. Understanding these risks is key for security professionals defending against Spooling attacks.
-
Common Types of Spooling Attacks
-
Print Spooler Spoofing
Hackers can masquerade as a legitimate network printer or print server to stealthily intercept print jobs as they pass through the spooler system. This data theft technique allows attackers to gain access to sensitive documents like financial reports or customer records.
-
Print Job Manipulation
By compromising the integrity of print jobs sitting in the queue, attackers can modify or inject malicious code into the jobs. When unsuspecting users later print the tampered jobs, the attacker’s code executes – anything from stealing files to installing malware.
-
Print Job Capture
Spoolers temporarily store print job data, which can contain sensitive information like usernames, passwords, or personal customer details. Savvy attackers sniff out these juicy details directly from the spooler’s cache as jobs pass through.
-
Denial of Service (DoS)
Overwhelming the print spooler with a barrage of fake print requests can grind it to a halt. This flooding knocks the spooler offline, preventing legitimate print jobs from completing. The resulting downtime and disruption torpedoes user productivity.
-
Remote Code Execution (RCE)
Finding and exploiting buffer overflow or other bugs in the spooler service gives attackers an in to run arbitrary malicious code right on the server. Owned by RCE, the server becomes a launchpad for the attacker to penetrate deeper into the network.
-
Privilege Escalation
Popping the spooler service can also yield elevated permissions to access higher-value targets. Cracking weak spooler passwords or leveraging vulnerabilities allows the attacker to gain admin-level privileges across the system.
-
The Impact of Spooling Attacks on Businesses
Successful Spooling attacks can cripple businesses. Breaches of sensitive data can lead to catastrophic financial and reputational damages.
For example, identity fraud stemming from data breaches affected 42 million U.S. adults in 2022, tallying a whopping $52 billion in losses, according to Javelin Strategy & Research. Even when businesses try to protect internal files, customer data stored in vulnerable third-party systems remains exposed.
Furthermore, denial-of-service attacks that disrupt Spooling can cripple productivity by preventing access to printing and other critical services that rely on smooth data flow. Users cannot perform essential duties without these resources.
In summary, failing to safeguard Spooling infrastructure against threats, both external and internal, can have severe consequences for any organization. Proactive Spooling security and monitoring are essential to avoid the disastrous fallout of successful attacks.
Best Practices for Secure Spooling
a. Secure Configuration of Spooling
Securely configuring Spooling systems is crucial to avoid vulnerabilities. Settings like proper queue permissions, encryption of spooled data, and disabling unnecessary services thwart potential attack vectors. For example, encrypting print spooler files protects sensitive documents should an attacker gain access to the queue.
b. Regular Monitoring and Updating of Spooling Processes
Keeping a close eye on Spooling activity helps detect threats early. Monitoring for abnormal surges in Spooling requests, suspicious files in queues, and unauthorized config changes allow a rapid response. Regularly updating Spooling software and OS patches also maintains a robust security posture.
Following the mantra of “if it ain’t broke, improve it anyway” for Spooling processes pays dividends. Partnering with a firm CCS learning academy for Level Up 360° – Group Training Program provides turnkey training to equip IT teams with the forensic skills to scrutinize systems. Their Level Up 360° – Group Training Program ensures personnel can monitor and tune Spooling for peak performance.
With routine maintenance and training, organizations can keep Spooling infrastructure purring smoothly while dodging cyber threats. Remember, an ounce of prevention is worth a pound of cure when it comes to securing these sensitive pathways.
c. Employee Awareness and Training Regarding Spooling
Educating employees about secure Spooling practices is critical, given insiders can be a top source of security incidents. As Cybersecurity Ventures points out, by 2027, organizations are projected to spend $10 billion globally on cybersecurity training as the workforce and digital adoption grow.
Building this security-centric culture makes employees the organization’s eyes and ears on the front lines. Even simple awareness, like not storing sensitive documents in Spooling areas, chips away at the insider threat.
With training, savvy employees become an invaluable line of defense in depth. Combining workforce education with the proper technical controls arms organizations to contend with the rising tide of cyber security spooling attacks.
Advantages and Disadvantages of Spooling in Cybersecurity
-
Benefits of Spooling Implementation
Here are some key benefits of implementing robust Spooling security:
- Data protection – Safeguards sensitive documents and data in spooler queues, preventing leaks of intellectual property, financials, and personal information to avoid catastrophic data breaches.
- System integrity – Maintains the stability and security of systems by blocking injection of malware through spooler and thwarting unauthorized access attempts. Avoids stability issues, data destruction, and total compromise.
- Network fortification – Strengthens the network by closing off the spooler vector as an entry point for wider attacks. Stops breaches in their tracks rather than letting them fan out across connected systems.
- Service continuity – Ensures uninterrupted printing and other spooling-dependent services by preventing denial-of-service disruptions that freeze operations. No interruptions mean no financial losses.
- Privilege control – Halts privilege escalation in its tracks by fixing spooler vulnerabilities that allow elevated permissions. Limits attacker access to higher-value assets.
- Regulatory adherence – Ensures compliance with mandates and data regulations through proper data protections and access controls on spoolers. Avoids fines, lawsuits, and reputational damage.
- Proactive defense – Provides an advanced line of defense against new and emerging spooling attack methods. Stays a step ahead rather than playing catch-up with hackers.
-
Potential Downsides and Risks of Spooling
Here are some potential downsides and risks associated with Spooling implementations:
- Increased attack surface – Spooling systems create additional points of entry for attackers that must be secured. More layers mean more complexity.
- Performance overheads – Heavy Spooling activity can tax server resources and degrade performance if not tuned properly.
- Difficult troubleshooting – Debugging Spooling issues can be tricky, given multiple interconnected components.
- Single point of failure – Outages in a central Spooling server can paralyze dependent systems and processes.
- Insider threats – Rogue employees can exploit Spooling weaknesses more easily with internal access.
- Compliance risks – Insecurely managed Spooling could fail data protection audits.
- Legacy hazards – Outdated Spooling software lacks modern safeguards and is prone to vulnerabilities.
- Cascade effects – Successful Spooling attacks provide footholds for further network infiltration.
- Recovery challenges – Rebuilding a corrupted Spooling subsystem requires specialized expertise.
Maintaining rigorous Spooling security is essential to keep risk exposure in check.
Conclusion
Spooling plays a crucial role in the cybersecurity domain. When implemented securely, it provides vital optimization of workflows. However, Spooling also introduces risks if not properly safeguarded, as its pathways can be exploited to breach sensitive data or disrupt operations.
Looking ahead, bolstering Spooling security will remain imperative as attacks grow more advanced. Spooling systems must evolve with emerging technologies like the cloud and AI/ML to manage new risks. But the core imperatives of access controls, encryption, and monitoring will continue to be cornerstones of robust Spooling cybersecurity programs.
By ensuring security is baked into spooling developments from the ground up, we can allow these pivotal processes to do what they do best – enabling performance, reliability, and scalability. With rigorous security foundations and continued vigilance, Spooling will keep catalyzing technological progress without introducing compromises. The key will be a proactive collaboration between cyber experts and spooling developers to realize this shared vision.
Jumpstart your cybersecurity career aspirations with CCS Learning Academy’s acclaimed CISSP certification training. This comprehensive course prepares you to pass the CISSP exam and reap the rewards of this gold-standard cyber security certification.
Ready to climb to the top tier of cyber security? Let CCS Learning Academy be your guide on the future-proof career journey. Contact us today to start mapping your path to career ascent.
FAQs
1. What is spooling in the context of cyber security?
Spooling refers to the process of temporarily storing data, often print jobs or emails, in a buffer before it’s sent to its destination. In cyber security, spooling can be a potential vulnerability if not properly secured, as it can be an entry point for attacks.
2. Why is spooling considered a potential security risk?
Spooling systems create temporary storage areas for data, which can be targeted by hackers. If not properly secured, attackers can intercept, manipulate, or inject malicious code into these spooled data, leading to data breaches or system compromises.
3. What are the advantages of spooling in cyber security?
When properly managed, spooling can streamline processes, reduce wait times, and ensure smoother data transfers. It also allows for better management and prioritization of tasks, especially in environments with high data traffic.
4. How can organizations safeguard their spooling processes?
Organizations can implement encryption for data in spooler queues, use authentication protocols, regularly patch and update spooling software, and monitor spooling activities for any anomalies.
5. How does spooling relate to print security?
Spooling is often associated with print jobs. If a hacker gains access to a spooler queue, they can intercept print jobs, which might contain sensitive information. Ensuring print security involves securing the spooling process.
6. Can spooling be used as a method for a Denial-of-Service (DoS) attack?
Yes, attackers can target spooling systems to flood them with excessive data or tasks, causing a system to freeze or crash, leading to a DoS condition.
7. How does fixing spooler vulnerabilities help in regulatory compliance?
Many regulations mandate the protection of sensitive data. By securing spooler vulnerabilities, organizations can ensure data integrity and confidentiality, adhering to compliance requirements and avoiding potential fines.
8. Are there any tools available to monitor and secure spooling activities?
Yes, several cyber security solutions offer spooling monitoring and protection features. Organizations should research and choose tools that fit their specific needs and infrastructure.
9. How often should spooling systems be audited for vulnerabilities?
It’s recommended to conduct regular audits, at least annually, to identify and address potential vulnerabilities. However, the frequency might increase depending on the organization’s data traffic and sensitivity.